1. The recipient opens the attached ZIP file to read the fake document in it. 2. The document contains a macro or some other active content that will unpack the stenographic content. This content, is typically the keylogger/backdoor Trojan combination used for phishing attacks. 3. The software resides on the […]
Daily Archives: December 5, 2018
3 posts
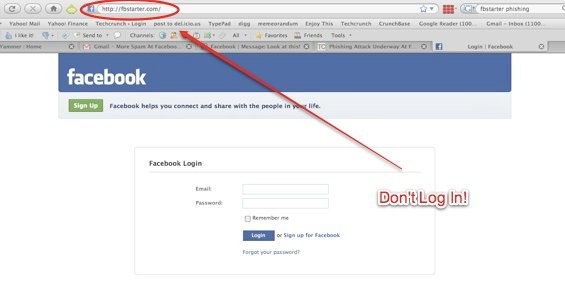
Cybercriminals are finding new and better ways to use facebook to phish for potential victims. Facebook has gone to great lengths to reduce spam, Fake News, phishing and other scams, but Facebook has risen to the second highest site for phishing attack, with Yahoo being the first . A common phishing […]
Phishing was originally used to describe email attacks designed to steal your online banking username and password. However, the term has evolved to now refer to almost any email-based attack. Phishing uses social engineering, attempting to fool you into taking an action. These attacks often begin with a cyber criminal […]