The terms EHR and EMR are often used interchangeably. The electronic health record (EHR) is a more longitudinal collection of the electronic health information of individual patients or populations. The EMR, in contrast, is the patient record created by providers for specific encounters in hospitals and ambulatory environments, and which […]
Blog
I took a full backup of a wordpress website and i suddenly felt the backup was taking too long… 900mb for more than 2hours… It couldn’t be the internet connection because i could stream videos. When i take wordpress backups i intermittently refresh the website (this might be a wrong […]
Asset tags are permanent-adhesive labels that companies and individuals use to track equipment for easier management and quicker processing. The tags may contain barcodes, serial numbering, company contact information and the like. Why Tag Your Equipment? Asset labels, especially those with QR or barcodes, let you follow an item through […]
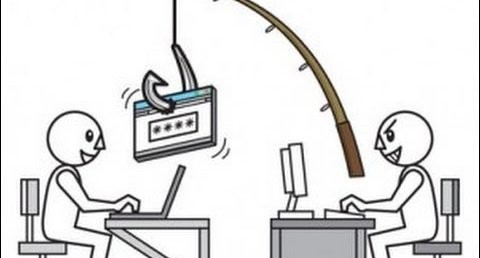
Phishing attacks are emails sent by cyber criminals to millions of potential victims around the world designed to fool, trick or attack them. These messages often appear to come from someone you may know. Clicking on a link in a phishing email you may be taken to a malicious website […]
Back Up!!! The easiest solution to ransomware is to prevent the consequence in the first place. A good backup/ disaster recovery procedure should be in place to recover as much data as possible before they were compromised. This comprises having daily/weekly/monthly, multiple copies of essential company data. An additional line […]
1. The recipient opens the attached ZIP file to read the fake document in it. 2. The document contains a macro or some other active content that will unpack the stenographic content. This content, is typically the keylogger/backdoor Trojan combination used for phishing attacks. 3. The software resides on the […]
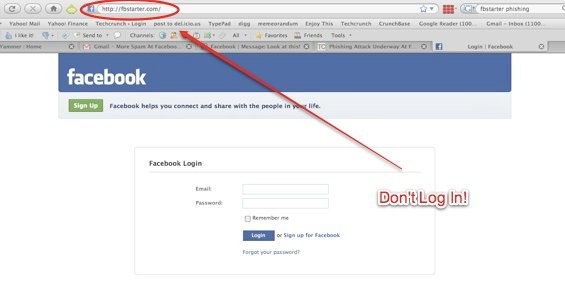
Cybercriminals are finding new and better ways to use facebook to phish for potential victims. Facebook has gone to great lengths to reduce spam, Fake News, phishing and other scams, but Facebook has risen to the second highest site for phishing attack, with Yahoo being the first . A common phishing […]
Phishing was originally used to describe email attacks designed to steal your online banking username and password. However, the term has evolved to now refer to almost any email-based attack. Phishing uses social engineering, attempting to fool you into taking an action. These attacks often begin with a cyber criminal […]
Ransomware is computer malware that installs covertly on a victim’s computer. The malware executes a cryptovirology attack that adversely affects it. The malware then demands a ransom payment to decrypt it or not publish it. Simple ransomware may lock the system and display a message requesting payment to unlock it. […]