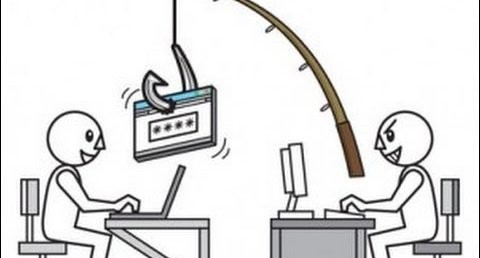
Phishing was originally used to describe email attacks designed to steal your online banking username and password. However, the term has evolved to now refer to almost any email-based attack. Phishing uses social engineering, attempting to fool you into taking an action. These attacks often begin with a cyber criminal sending you an email pretending to be from someone you know or trust, such as a friend, your bank or your favourite online store. These emails entice you into taking an action, such as clicking on a link or opening an attachment. Cyber criminals craft these emails to look convincing, sending them out to literally millions of people around the world. The criminals do not have a specific target in mind. They simply know the more emails they send out, the more people they may be able to fool.
Phishing attacks:
• Harvest Information:
The cyber attacker tries to fool you into clicking on a link and taking you to a website that asks for your login and password, or perhaps your credit card or ATM number. These websites look legitimate but they are fake websites designed by the cyber attacker to steal your information.
• Infect your computer with malicious links: An Email with a malicious link is sent to the Victim. If you click on the link, you are directed to a website that silently launches an attack against your computer that will infect your system with malicious software.
• Infect your computer with malicious attachments: These are phishing emails that have malicious attachments, such as infected PDF files or Microsoft Office documents. If you open these attachments they attack your computer and gives the attacker complete control over the computer.
• Scam: These are attempts by criminals to defraud you. Notices that you’ve won the lottery etc are scams created by cyber criminals who are after your money.
PROTECTING YOURSELF
In most cases, simply opening an email is safe. For most attacks to work you have to do something after reading the email (such as opening the attachment, clicking on the link or responding to the request for information). Here are some indications if an email is an attack:
• Be suspicious of any email that requires “immediate action” or creates a sense of urgency. This is a common technique used by criminals to rush people into making a mistake.
• Be suspicious of emails addressed to “Dear Customer” or some other generic salutation. If it is your bank they will know your name.
• Be suspicious of grammar or spelling mistakes; most businesses proofread their messages carefully before sending them.
• Do not click on links. Instead, copy the URL from the email and paste it into your browser. Even better is to simply type the destination name into your browser.
• Hover your mouse over the link. This will show you the true destination where you would go if you actually clicked on it. If the true destination of the link is different than what is shown in the email, this may be an indication of fraud.
• Be suspicious of attachments and only open those that you were expecting.
If after reading an email you think it is a phishing attack or scam, simply delete the email.